Strict password requirements could be hurting your signup conversion
Suppose you have most of the signups coming from Single Sign-On (SSO), usually seen in websites as sign-on with Google or Facebook. In that case, you are probably in a great place already because all security concerns are offloaded to specialists (assuming they are continuously improving and releasing security patches). However, if for different reasons, whether being because in some fields users are not accustomed or don’t trust SSO, you might want to revisit your password requirements to not miss out on prospects.
Let’s face it, before the introduction of SSO, you were probably annoyed at some point when you were required to enter a complex password. Even worse, the user interface just tells that your password doesn’t meet the requirements only after you press enter. We are accustomed to our reusable and convenient password; every time we have to compose a new password, we might just give up because the requirements are too strict. If we do end up finishing the signup process, we have already started our trial with negative impressions.
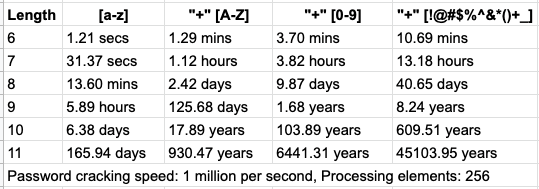
So, does the signup process have to be that complicated? What can the engineers do to make that process smooth and frictionless? Why do we need complex passwords? It pretty much comes down to the time it takes for a computer to test all possible combinations (brute force) to crack a password. Following is a quote containing details about passwords in average. Note that the regular password usually doesn’t have any special characters.
"Most of the passwords (61%) were right at the password limit, either 8 or 9 characters long. The average length was 9.6 characters, and the average password consisted of 1.1 upper-case letters, 6.1 lower-case letters, 2.2 numbers and 0.2 special characters. (source)"
Now, let’s put together some estimates from online sources. Let’s say we have a graphic card with 256 independent cores, and each core can test 1 million combinations per second. The table below illustrates how much time it would take to crack passwords containing 6 to 11 characters in length, and each column shows that time if upper-case, numbers and special symbols are added to the mix.
To make it harder for hackers to crack a password using brute force, should we pick a longer or a short password that must include numbers and special characters? For us, the answer was: let’s follow the principles of the book Don’t Make Me Think, let’s pick the average password length that users are accustomed to (8–9 characters) and integrate other mechanisms to protect their accounts.
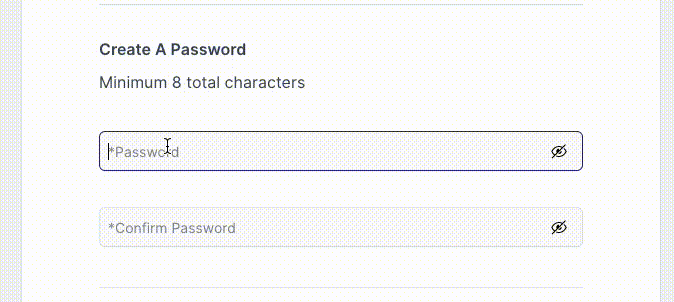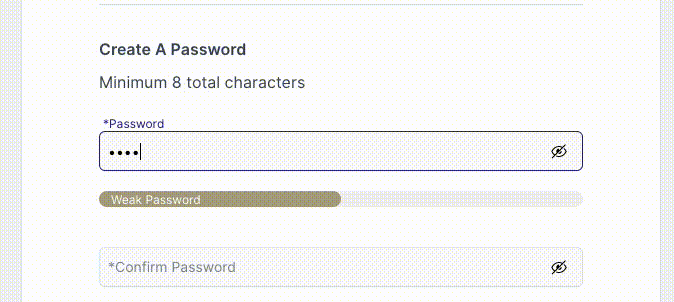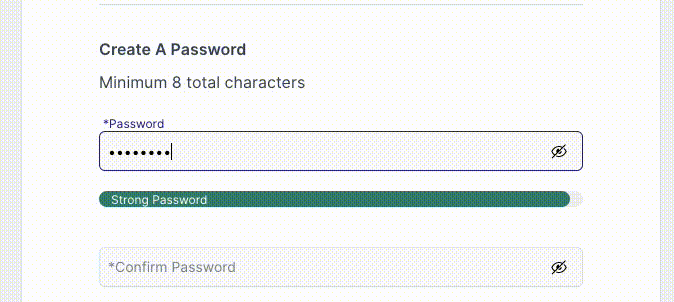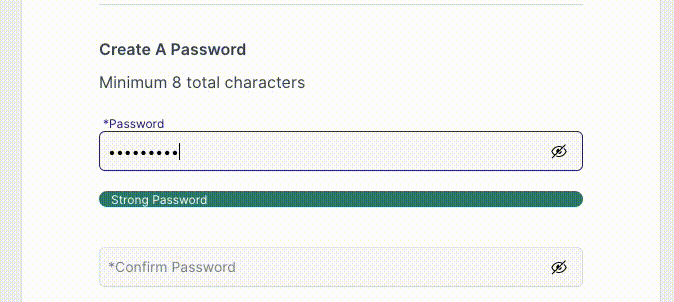
Following is a gif illustrating what the signup and its password requirements used to look like: at least eight characters, one number, one upper-case letter, and one lower-case letter.

And the next gif illustrates a simplification of the password requirements to a minimum of 8 characters, no other restrictions, which resulted in an enormous increase of around 15% in signups.
What can be done from an engineering perspective to reduce password requirements but, at the same time, maintain all accounts extremely secure?Following are some solutions:
- API rate limiting: This could be either pretty simple or quite complex, depending on your current technology infrastructure. The idea behind this is to limit the number of password combinations that can be tested per second, exponentially increasing the time that it would take to crack a password.
- Try again in a few minutes: This is a low effort mechanism that can be implemented with an in-memory time-based cache. The idea behind this is to keep track of how many failed login attempts happened in a given time window. After a certain number of unsuccessful attempts, new login attempts are disabled for a few minutes.
- 2 factor authentication(2FA): This is a medium effort mechanism that requires the integration of third-party tools. After entering your password, you receive a random code through SMS or email for another authentication step. It massively increases security, but it also increases friction. It’s usually an optional step, and not everyone likes it (even though the adoption of 2FA has been rising over the years — 53% in 2019).
- Identifying suspicious activities: This is another medium to high effort mechanism that requires the integration of third-party tools (Auth0, for example). Have you ever received an email asking, “was this you”? Login attempts are blocked if deemed anomalous (whether from another place or a different computer, for example). These systems are much more advanced, and they offer much lower friction than 2FA systems, assuming that your customers don’t share their computer with anybody else.
If your team has time to implement all the apparatus to protect your customers, please do it, security is never enough, and your customers will appreciate it. Also, always remember, don’t make your customers think; make us (the engineers) think, and enjoy the increase in conversions.
I hope you enjoyed this article! Have a great day!